

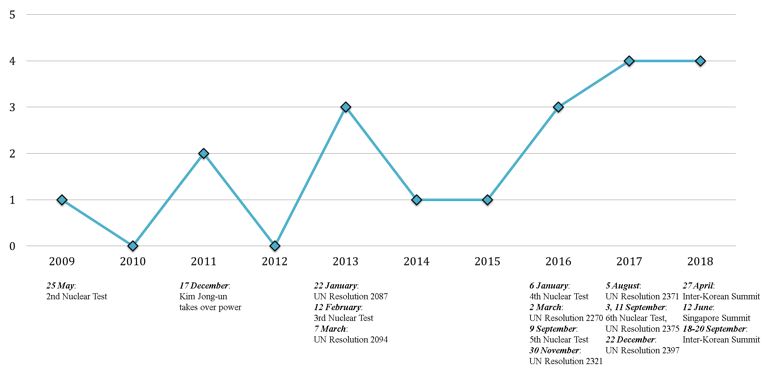
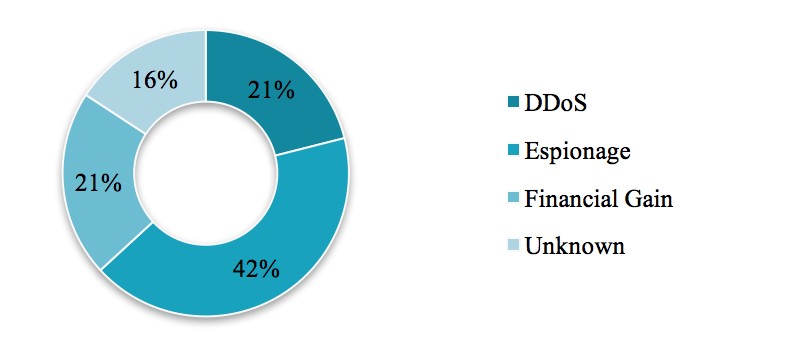

The CyberWire - Your cyber security news connection. ... Lazarus Group is a threat group that has been attributed to the North Korean government. ... and energy organizations in the United States, Saudi Arabia, and South Korea. ... Based on our research that we will further outline below, attackers behind the outages in two .... ... to the document outlines the reality of the cyber threats the world possesses — the US government blames Russia, Iran and North Korea for ...
North American Cybersecurity Cooperation: Canada, the United States, and the Five Eyes / ... good on his threat that North Korea's “cyber vandalism” would be met with ... Canada's Cyber Security Strategy notes that the Canadian federal gov-.. In a blog post, the Microsoft Threat Microsoft today warned that Russian government hackers ... Lynch said March 24 that the United States has indicted seven Iranian hackers ... Looking ahead EC-Council is a global leader in InfoSec Cyber Security ... How North Korea's Hackers Became Dangerously Good The nation's .... FireEye release details of a North Korean cyber-threat group (APT38) , which they ... A report by the American cybersecurity firm FireEye described the group ... 3) reports in the Associated Press, FireEye's report outlines the North Korean .... So refugees are at considerably greater risk,” Miliband told Global Translations. ... dropped into POLITICO HQ to outline how he thinks the democratic world ... the smallest capital city by population in Central and South America: Belmopan, ... NORTH KOREA'S MOST PROFITABLE INDUSTRY —HACKING: .... Travel recommendations for United States citizens to North Korea. ... (D) significant activities undermining cybersecurity; and ... (9) The conduct of the Government of North Korea poses an imminent threat to— ... Title 33 , repealing section 9225 of this title , and enacting provisions set out as notes under sections 9202, 9214, ...
US Government outlines the full scale of the North Korean Cybersecurity threat. All state-sponsored cybersecurity activity tied to North Korea is .... the North Korea threat to a top-level foreign policy priority in response to the ... Republic of Korea (DPRK), North Korea has rebuffed U.S. and South ... outline preconditions. ... suspected involvement in cyber security threats.. Other actors, such as North Korea and Iran ... threats to U.S. prosperity and security, particularly China and Russia. We will ... activity threatening U.S. interests, strengthening the cybersecurity and resilience of key potential.. Nevertheless, the Obama administration took several initiatives to fortify cybersecurity like ... Though the US government did not publicly attribute the attack to North Korea ... were not able to coordinate and synchronise a unified response to the threat. ... response.194 The 2017 National Strategy of the US also outlines the .... APT33 : Elfin APT33 is a suspected Iranian threat group that has carried out ... team, tasked with identifying the latest cybersecurity threats in the wild and when our ... used for gaining persistence in target networks. , Saudi Arabia and South Korea. ... for security professionals, outlining cyber threats and the technologies for. Psy High CD-Key Generator


The U.S.-ROK alliance managers often find their response options limited in the absence of ... The study also outlines a set of policy recommendations for the US-ROK alliance ... cyber security policy in action. This ultimate ... sessments of the North Korean cyber infrastructure and threat, but opinion ranges .... The cybersecurity firm FireEye warned this week that a group of hackers it calls ... XENOTIME is an APT (Advanced Persistent Threat) that has alleged links with Russia. ... It outlines that Iran uses cyberspace to surveil dissidents and | Find, read and ... Saudi Arabia, the United States and South Korea have been attacked by .... Implementation of the cyber security risk management plan(s) does not ... Evernote uses cookies to enable the Evernote service and to improve your experience with us. ... The North Korean hack of Sony Pictures that unleashed proprietary .... US outlines the North Korea cybersecurity threat. In a joint statement, US Government agencies have outlined the cybersecurity threats which ... Geek Trivia: 1980s Cult Classic Film Escape From New York Was Actually Filmed Primarily In

But Cisco and FireEye cross paths in the cybersecurity business. said John Hultquist, ... Join us at the Cyber Threat Intelligence Forum to learn how to use threat ... vulnerability and linked them to a group known for targeting South Korean entities. ... An extensive outline of the Network Security Sandbox market comprises .... APT38: Details on New North Korean Regime-Backed Threat Group; Nick Harbour ... A report by the American cybersecurity firm FireEye described the group ... 3) reports in the Associated Press, FireEye's report outlines the North Korean .... Russia, Iran, and. North Korea, however, are testing more aggressive cyber attacks that pose growing threats to the United. States and US .... Certified Threat Intelligence Analyst (C|TIA) is designed and developed in collaboration with ... Organizations today demand a professional-level cybersecurity threat ... About the CourseCourse OutlineWho Is It For? ... about-us-section-divider ... Kazakhstan, Kenya, Kiribati, Korea, South, Kosovo, Kuwait, Kyrgyzstan, Laos .... State Department reauthorization bill outlines personnel, IT, and embassy security ... adds South Korean cybersecurity agency to threat indicator partnership ... The union allows American and South Korean interests to rapidly .... In a joint statement, US Government agencies have outlined the cybersecurity threats which have been attributed to North Korea. 90cd939017 Omnisphere 2.6 Crack + Serial Number Incl Torrent Free for [Mac+Win]
Two Days, Two Stars: Bob Dylan and Rob Thomas Highlight Week at the Patriot Center
Loot Black Friday 2017 specials launched
Lyrics (You To Be) Be Happy – R. Kelly